TMPSYS-Crypto Secure Network
Main concerns
Complexity
- How can a device know the IP address of another device?
- How can a device know whether a full data path exists to and from another device?
- How can a device trust that all exchanged data is delivered to the other end?
- How can a device know that the IP addresses will not change? What will be the impact on the communication if they do?
Security
- How can a party be sure about the other party's identity?
- How can the parties trust the network intermediate elements which transport the communication data? How can they be sure that data is not filtered or altered or replaced?
- The communication can be secured and take place if the two (or more) parties share a common secret (or if they are able to create a new one), but how can they be sure that such secret is known to them only? How can they agree on the secret to use without disclosing it?
Main features
Network size 10k-20k users
Protocol TCP/UDP
Communications Up to 16 secure channels per user
Messaging IP-based
Store & Forward
Security Higher
Secure token Proprietary
Customization Yes
Client-Server architecture: client elements connect and authenticate with a server
- Client to Server
- Server to Server
Clustered architecture: clients are handled by multiple coordinated servers
- Performances
- Redundance
Pipe-based communication: clients exchange communication data within pipes
- Multiple pipes per client
- Data-agnostic server
Pass-through data routing: pipes traverse servers in order to support private networks
- NAT, firewalls, ...
Multi-protocol support: TCP/UDP
Network components
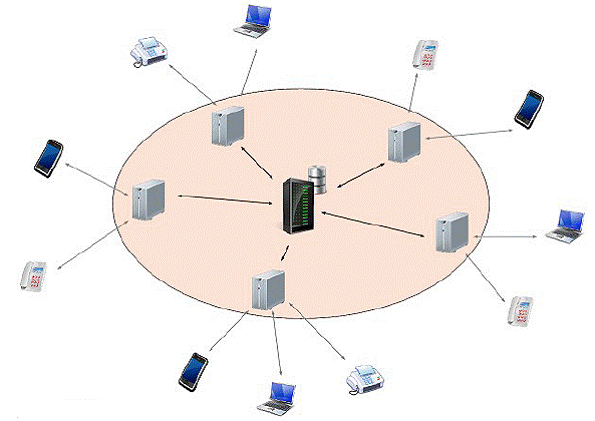
Cluster Manager [1]
Network core, authenticates the other components and validates all communications
Satellite Server [1 → N]
Manages client requests, routes pipe data
Client [N]
End-user's equipment, able to establish communications with other clients
Store & Forward [1]
Manages the storage of all pipe data sent to offline receivers, and subsequent deliveries when they connect
Admin Client [1]
Manages Hardware Identities and updates clients Remotely
KMS – Key Management System
MSE management
- Provisioning: MSE keys injection, policies, application settings, …
- Add/modify/remove
User management
- Personal information, phone number, MSE devices
- Add/modify/remove
Group management
- Add/modify/remove
Group Keys management
- Generation/Renewal
- Expiration
Local/remote distribution
- Key update, policy update, zeroize, ...
Auditing
- Operation logs
KMS – Main features
Remote Communication Key updates Yes
Remote zeroize Yes
Users Up to 10k-20k
MSE/user decoupling Yes
Remote policy updates Yes
Contacts updates Yes
Operators Multiple
Auditing Yes
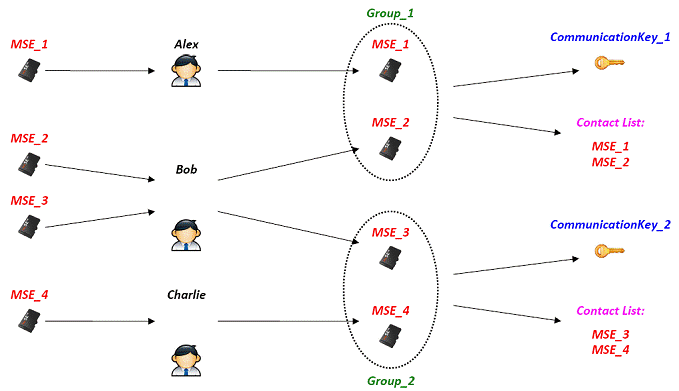
KMS – Simple scenario (A)
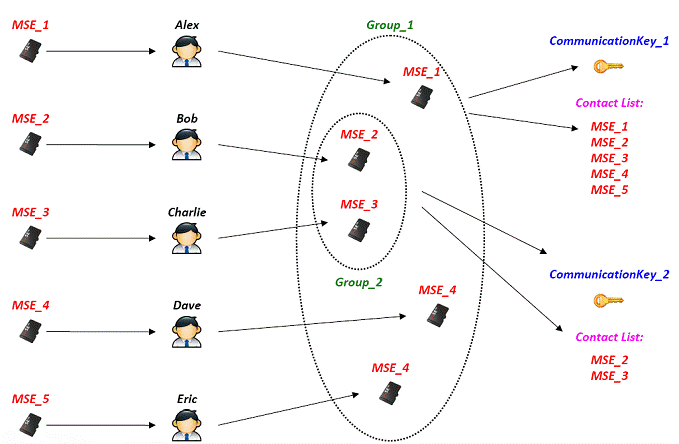
KMS – Simple scenario (B)
xSE – Secure Environment
xSE main features
HW crypto engine
Integrated memory
Internal keys database
No drivers
Strong authentication
Standard & custom security functions
USE – USB Secure Environment

MSE – Micro-SD Secure Environment

MSE – Micro-SD Secure Environment
Common xSE features
SD card interface (up to 5 Mb/s)
Standard and custom
algorithms
Designed for Mobile
Applications
Voice processing
Low Power mode
Integration ready
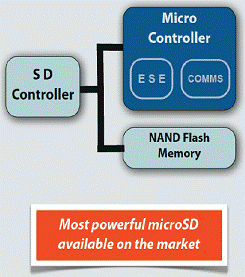
MSE – General architecture
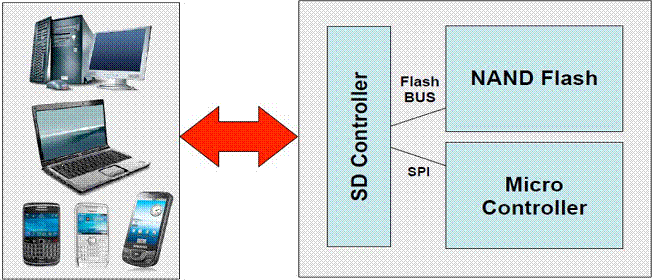
MSE – Hardware architecture
Micro Controller
- 160 MHz - floating point unit
- FLASH 1 MB
- RAM 192 KB
- Dynamic power scaling
COMMS
- a complete range of communication functions
SD Controller
- compatible with mobile and computer OS
NAND Flash Memory
- 2 GB
MSE – Virtual file (file I/O) approach
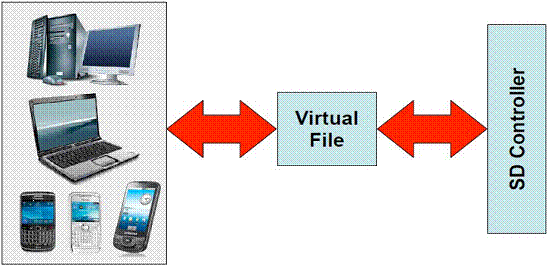
The Virtual File is an intercommunication
channel between the Host and the SD
Controller.
It is open in Pass Through Mode:
- No OS Buffering
- No OS Caching
MSE – Security functions
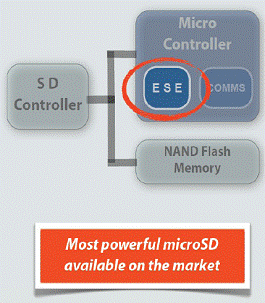
Native Security Functions
- AES256 8Mb/s internal speed
- AES modes ECB - CBC - OFB
- up to 32 parallel sessions
- Asymmetrical functions
- Public Key RSA 2048 – 4096 FIPS 186-3SP800-56B
- X.509 certificates (based on AES 256)
- Public and private key generation
- Diffie Hellman
- Elliptic Curves up to 571 Koblitz
- Authentication Functions
- Internal physical RNG FIPS 140-2
- Custom algorithms on demand
MSE – Communication functions
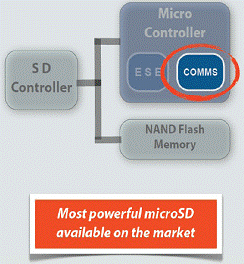
Full set of communication functions to ease integration
- Vocoders
- 4.8 Kbps optimized for mobile
- G729 - 8Kbps
- Native implemented communication protocols for
- comm parameters negotiation
- encryption key negotiation
- transport voice & data protocol for IP channels
MSE – Customization
Customization can be achieved by injecting proprietary algorithms that the customer can develop (compile, inject and test) independently from the OEM.
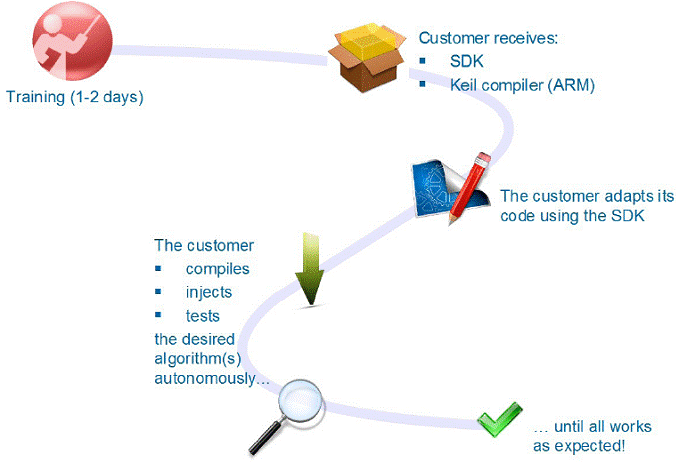
The MSE is designed to be customized by the customer through its own private algorithms.






















